Vulnerabilities are highly sought after by attackers who use them to launch all kinds of nefarious activities, such as stealing data, implanting ransomware, escalating administrative privileges or launching advanced attacks.
A modern enterprise network can hold thousands or even millions of vulnerabilities, more than a large IT team could likely ever fix. And for many state governments with federated IT operations, this can be an even bigger issue as the hodgepodge of semi-independent agencies and organizations each contribute their own unique stack of vulnerabilities to that mix.
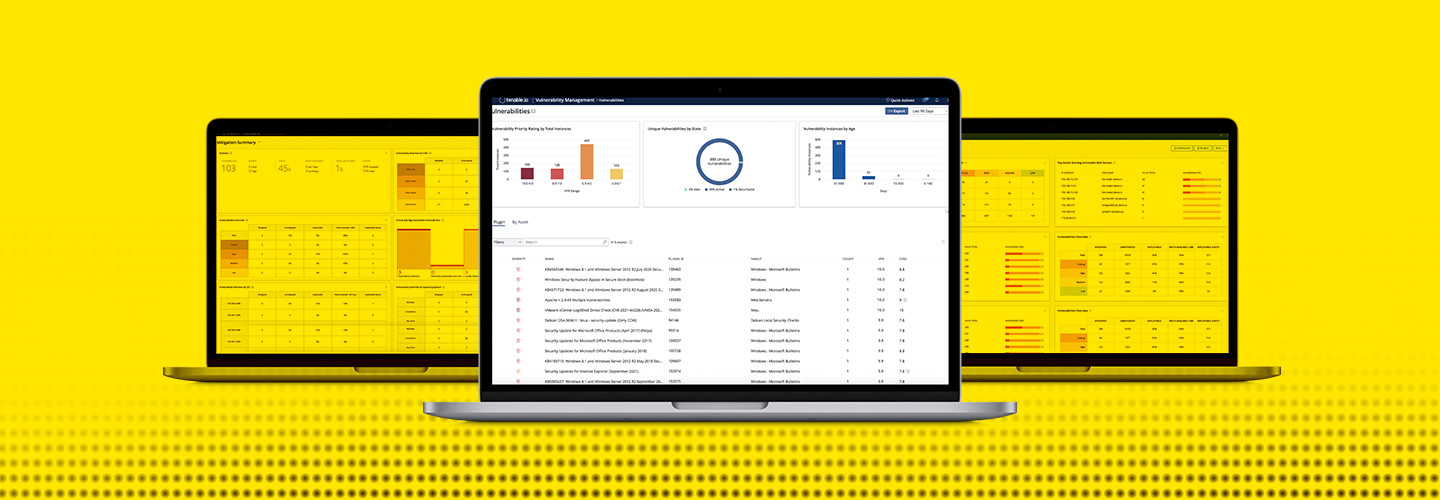
The Tenable Vulnerability Management platform (formerly Tenable.io) is deployed as a service and was designed to manage environments that are saturated with potential risks. It not only finds vulnerabilities but also is smart enough to prioritize which ones need to be fixed right away and which can wait until IT teams have time to address them.
Click the banner below for more on a proactive approach to maintaining a strong security posture.
Software Always Actively Searches for Problems
To locate vulnerabilities, the platform uses a combination of active scanning agents, passive monitoring and cloud connectors — and it is always actively searching. So, it can find new vulnerabilities quickly if, for example, a state agency connects a new device to the enterprise network or spins up a new cloud instance.
Armed with a list of thousands of discovered vulnerabilities, the Tenable Vulnerability Management platform applies machine learning, data science, threat feeds and artificial intelligence to predict which fixes need to be made quickly before they can be exploited by an attacker. It does this by going beyond the typical Common Vulnerability Scoring System used by many vulnerability management solutions to ask additional risk-based questions.
The Platform Generates a Thorough Security Assessment
For example, the platform calculates how widespread a discovered vulnerability is within an enterprise, what assets are affected by the vulnerability and how easy it would be for an attacker to access and exploit it.
It also determines if there are any active threat campaigns involving that specific vulnerability occurring in the world and the potential damage that might occur if it were exploited. It then calculates an accurate Vulnerability Priority Rating score for IT teams to follow. In a test environment, the Tenable Vulnerability Management platform found over 700 vulnerabilities, but prioritized fixing only 27 of them; of those, 12 needed to be taken care of right away.
By going beyond the typical capabilities of a vulnerability scanner to fully prioritize the risk posed by individual problems, the Tenable platform can help state IT teams get ahead of their critical and dangerous backlog of vulnerabilities, fixing issues long before an attacker can exploit them.
SPECIFICATIONS
PRODUCT TYPE: Vulnerability management platform
KNOWN VULNERABILITIES DATABASE: 130,000 and expanding
USER INTERFACE: Web-based
DISTRIBUTION: As a service
LICENSE: Per seat or per user