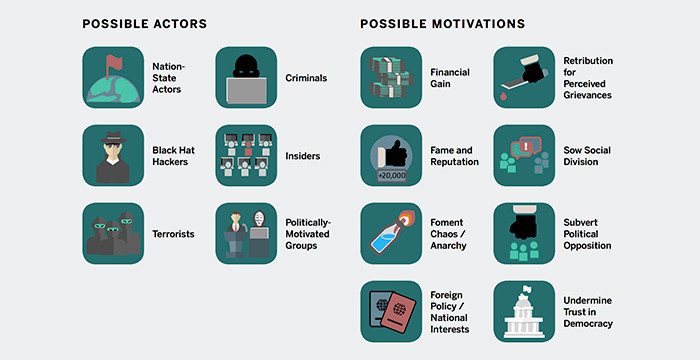
There are numerous malicious actors that have the motivation to attack state and local election infrastructure. Source: Belfer Center for Science and International Affairs
The report recommends that states make it mandatory for election administrators to report these instances when they occur to the Department of Homeland Security, the U.S. Election Assistance Commission and state officials.
In Georgia, Kelley testified, more than 6.5 million voter records and other privileged information were exposed due to a server error. The security vulnerability had not been addressed six months after it was first reported to authorities, “even though it could have been used to manipulate the state’s election system,” he said.
How to Build a Vulnerability Management Program
Vulnerability management is “the means of detecting, removing and controlling the inherent risk of vulnerabilities,” a SANS Institute guide notes. “The vulnerability management program utilizes specialized software and workflow to help eliminate detected risks.”
Vulnerability management comprises identifying and tracking assets to build asset inventories, categorizing assets into groups, scanning those assets for known vulnerabilities, ranking risks, engaging in patch management, testing patches, applying patches and conducting a follow-up remediation scan to confirm that the vulnerabilities have been addressed.
In the context of election cybersecurity, state and local election officials can turn to a variety of resources to conduct vulnerability assessments. One is the Elections Infrastructure Information Sharing and Analysis Center, which started in 2018 under the auspices of the Center for Internet Security.
EI-ISAC analysts work with trusted affiliates to conduct research and gather intelligence about cyberthreats targeting elections or elections-affiliated systems, according to the organization. The center then sends notices to members based on predetermined escalation procedures, and also offers recommended remediation steps and technical assistance.
For elections entities that are experiencing an expediting targeted cybersecurity threat, the EI-ISAC provides a free network and web application vulnerability assessment. “These assessments include a manual analysis and verification of vulnerabilities discovered, prioritized remediation steps, customized reporting, and remediation support,” the center says.
DHS’ Cybersecurity and Infrastructure Security Agency offers a range of cybersecurity assessments, including vulnerability scanning “of internet-accessible systems for known vulnerabilities on a continual basis.” As potential vulnerabilities are identified, CISA notifies the customer organization “so that preemptive risk mitigation efforts may be implemented in order to avert vulnerability exploitation.”
As part of its Protect2020 election security campaign, CISA says it is working to increase election officials’ awareness and participation in Domain-based Message Authentication, Reporting and Conformance (DMARC), Hyper Text Transfer Protocol Secure (HTTPS), CISA's free election services, EI-ISAC membership, and Albert sensor deployment.
VIDEO: These are the cybersecurity threats that keep state CISOs up at night.
Authenticated Scans vs. Unauthenticated Scans
In the world of vulnerability scanning, there are both unauthenticated scans and authenticated scans.
An unauthenticated security scan, also known as a logged-out scan, is the “process of exploring a network or networked system for vulnerabilities that are accessible without logging in as an authorized user,” TechTarget reports.
Such scans give agencies visibility into “what a malicious hacker could access without acquiring login credentials to pose as a trusted user,” the site notes.
Meanwhile, authenticated scans “determine how secure a network is from an inside vantage point,” TechTarget reports, and often discover “many vulnerabilities that cannot be detected through an unauthenticated scan.”
Authenticated scans help IT and security administrators figure out “what needs to be done to ensure that should an attacker gain access to the network or a user account, important accounts and data will be protected,” according to TechTarget. They also can limit the damage of insider threats.
What Are the Best Vulnerability Management and Testing Tools?
Election authorities have a wide range of vulnerability scanner tools at their disposal.
CDW offers comprehensive cybersecurity evaluations that include vulnerability assessments designed to “evaluate current IT systems to determine vulnerabilities that could be exploited.” CDW also offers penetration testing to perform “ethical hacking” and “identify vulnerabilities that cannot be found without significant manual analysis of poor passwords and chain-of-trust issues.”
There are also several leading vendors that provide vulnerability scanning and management tools. They include Nessus from Tenable, which features high-speed asset discovery, configuration auditing, target profiling, malware detection, sensitive data discovery and vulnerability analysis.
Another option is BeyondTrust Vulnerability Management, which, the company says, offers “context-aware vulnerability assessment and risk analysis” so that IT admins can put vulnerability data into an actionable context.