State Elections Agencies Focus on Voting Security Ahead of Midterms
During the last election, Russian cyberattackers looking for vulnerabilities scanned 21 state election systems, including those in Illinois, over the 2016 campaigns. While the Department of Homeland Security says the scanning activity did not necessarily breach systems, some individual states have reported compromised data.
This year, for instance, the Illinois State Board of Elections reported a 2016 breach of its voter registration system, detailing a SQL injection attack of unknown origin that exposed records in the state’s voter registration database.
Since the attack, the Illinois board has worked with state IT experts as well as DHS cybersecurity professionals to keep the database of 18 million records and the servers on which it resides safe from attackers, says Matt Emmons, the agency’s IT director. And there are plenty of hackers out there.
Securing voting systems is a major challenge because state election agencies often act as clearinghouses. A state’s voting jurisdictions may purchase and maintain their own equipment and hire their own employees. Still, states have responsibilities to educate every jurisdiction and to protect voter registration and the overall electoral process.
This is especially important since most states maintain aging election equipment, including voting machines. States have increased their investments in cybersecurity measures for their election IT systems, including purchases of multifactor authentication, perimeter sensors, email filtering and monitoring, threat scanning, information sharing systems and more.
“The most sophisticated threats we are facing are coming from outside the country,” Emmons explains. “We consider the threat of nation-state actors and their near limitless resources the most threatening issue today. Most federal law enforcement agencies believe the foreign meddling with our election systems is going to continue.”
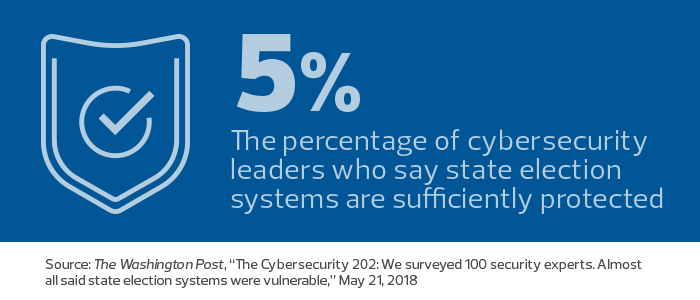
MORE FROM STATETECH: Find out what county officials can do to secure the 2018 elections!
Colorado Focuses on Endpoint Election Security
Colorado is mitigating the risk of attacks by nation-states and other actors with stringent IT requirements and policies, says Trevor Timmons, Colorado Department of State CIO. “We require that counties have endpoint protection software and not just anti-virus, but advanced malware prevention software for any machine that accesses the voter database,” he says. To make it easier, Sophos software is made available to Colorado counties at no cost. On the database side, data is encrypted.
Colorado also is taking a page from multinational companies and looking at social media and dark-web monitoring to find threats before they become a problem. Although it’s just getting started with the process, the state already has had some success with threat hunting.
Back in 2016, a security researcher boasted on Twitter about breaching one of Colorado’s ballot tracking systems designed to text or email constituents when their ballots were received. “He posted a photo purportedly of SQL tables behind the ballot tracking system. He said, ‘Hey, look I hacked this election system. Too bad they’re not really paying attention to security.’” The state reached out to the FBI, which discovered that there was no breach. “These are the types of real-world things that pop up and can impact voter confidence if they are left unchallenged and gain traction in the marketplace of ideas,” Timmons says.
Utah Partners with the FBI, MS-ISAC to Combat Threats
In Utah, where state IT resources are scanned between 200 million and 300 million times daily, various election offices have also doubled down on technology. Election offices have the benefit of Palo Alto Networks intrusion detection and firewalls as well as Cisco firewalls. “We also use Splunk for log aggregation, and that’s good for seeing anomalies and behaviors,” explains Utah CISO Phil Bates.
Most important, says Bates: The agency is constantly changing its security strategy. “We’re updating tools, changing the layers that we have and modifying things every day.”
The state launched its current IT strategy in 2012 when it created a cyber task force, partnering with its fusion center and bringing in experts from its state bureau of investigation and the FBI office in Salt Lake City. This year, the state upped the ante, bringing everyone together under one roof instead of trying to coordinate from different locations. The 26-person team still focuses on specialties — the fusion center is primarily responsible for intelligence gathering, for instance — and no one on the team is shy about tapping experts from other states, either.

“We partner with the Multi-State Information Sharing and Analysis Center, and they are a really good source for us,” says Bates. “If we see traffic in Utah that looks ugly, we send them to MS-ISAC and they can share with the other states, and vice versa. If another state sees something they know, they send it up to MS-ISAC. That way, we can change our posture when we know something’s out there.”
DOWNLOAD: Read this white paper to find out how to manage cybersecurity risks!
Election Officials Must Bolster Security and Public Trust
With all the news about attacks on U.S. elections, regaining trust before voters go to the polls next is crucial for state boards of elections, says Edgardo Cortés, election security adviser at New York University School of Law’s Brennan Center for Justice. “The 2016 elections were definitely a wake-up call that told states there were bad actors out there, and equipment and technology needs to be secured.”
It’s important to tell citizens that election administrators have performed security audits, identified potential vulnerabilities and educated stakeholders about those risks, Cortés says.
“Internally, we are taking cybersecurity training to anyone who is interested around the state, rolling out a cybernavigator program,” Emmons from Illinois says. “We do phishing awareness training and other work to defend against breaches and cyberattacks.”

States also should have contingency plans in place for websites, databases and other voting technology — because election agencies don’t get a second chance if something goes wrong on Election Day, Cortés says.
“Do your risk-limiting audits. Secure your systems. Make sure you have enough provisional ballots. Limit wireless capabilities of things like electronic poll books,” Cortés says. “Make sure you have enough bandwidth to handle election night capacity. Anticipate anything that could go wrong, because everything has to go off without a hitch.”










