Review: FireEye Email Threat Prevention Cloud Seamlessly Protects Government Email
FireEye Email Threat Prevention Cloud makes use of multiple techniques to stop spam, viruses and phishing threats before they invade government networks. Besides the usual anti-virus and anti-spam detection found in other products, FireEye’s solution contains impersonation detection, advanced threat protection, threat intelligence and the ability to write custom rules based on the YARA script language.
FireEye Government Email Threat Prevention is a Federal Risk and Authorization Management Program-authorized email security service, so state and local governments can adopt it with confidence. It simply sits between the originating servers and any on-premises or cloud-based email servers. More than 900 federal, state and local agencies worldwide already deploy FireEye solutions.
IT Admins Can Screen Threats with Ease
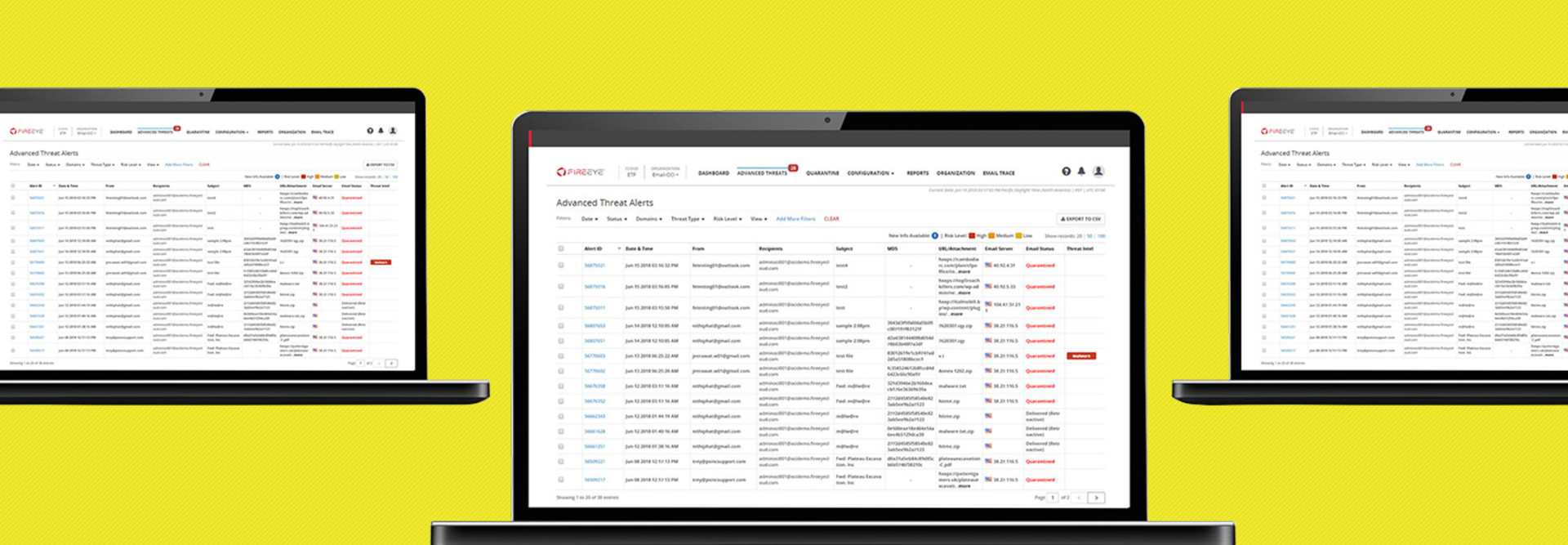
There are two main sections for administration of email security: Advanced Threat Protection and Message Details. Both dashboards are intuitive, and it doesn’t take long at all to navigate them.
Within the Advanced Threat Protection screen, administrators can easily search for specific alerts, determine the status of a malicious email, filter specific domains or status, view relevant information on individual threats or download information to a comma-separated value file for further review.
Users can quickly scan a list to see which threats were present in a specific time interval. By clicking on the individual alert ID, users see a summary of the alert, a hygiene analysis, and they can track the history of the alert and receive a link to relevant threat intelligence. It also reveals any URLs or attachments associated with that email.
Scan Messages for Threat Details
When someone clicks on a particular message, the Message Details screen appears. This screen contains the full details of the message and the threat.
Users can see full header information, the automated analysis report and details, any detected malware communication or operating system changes made, and all of the hygiene information. Users can also take action on the message: release it, delete it or download a copy of it into a password- protected encrypted case file.
Government Agencies Remain Particularly Susceptible to Email Attacks
Government organizations are increasingly at risk from cyberattack from foreign nation-states, cybercriminals and rogue activists. Groups such as APT29 use malware such as HAMMERTOSS to penetrate and create a foothold on targeted computers.
Email is still the No. 1 threat vector, but the game has changed: It’s no longer just random nuisance emails but rather targeted attacks against specific individuals, called “spear phishing” because of its selective approach.
In its “M-Trends 2019” report, FireEye Mandiant predicted email would remain a common source of attack for bad actors, who will evolve their tactics, techniques and procedures with increasingly sophisticated security tools and monitoring. According to FireEye, as of 2018, 269 billion emails are sent globally every day, and 91 percent of all cybercrimes begin with an email.
“Organizations will need to adapt their email defenses and monitor attacker techniques to improve their detection and response capabilities. This will require continued vigilance ... and appropriate security solutions aimed at detecting malicious links or attachments in emails,” the report states.
Impersonation detection becomes particularly valuable for government organizations vulnerable to phishing. As the National Association of State Chief Information Officers notes in its 2018 “State Identity Credential and Access Management Guidance and Roadmap,” effective security measures must guarantee “identification of the information requester and supplier.”
“This is of vital importance in an environment where phishing, scamming, and identity theft are rampant,” the report adds.
FireEye Email Threat Prevention Cloud
Hosted Service Type: Software as a Service
Installation Type: Hosted
Compatability: PC
Licensing: Subscription license
Compliant: ISO 27001 compliant and SOC 2 Type 2 compliant
Good Governance: Meets FISMA requirements and NIST guidance