Secure IoT Essential to Smart Transportation's Future
In an idealized version of future roadways, cars and buses zip along with minimal traffic or accidents, using automation and connectivity tools to anticipate and prepare for everything from changing traffic signals to patches of black ice. In a darker scenario, hackers leverage those new connections to infect vehicles and infrastructure — causing gridlock by turning all of a city’s traffic lights red, spying on drivers through their cars or even demanding ransom payments in exchange for releasing control over a bus’s steering or braking system.
Until recently, such gloom-and-doom visions have been largely hypothetical, but as Internet of Things (IoT) pilot programs begin to hit highways around the country, these concerns are poised to begin playing out in the real world.
Hackers could attack radio-controlled smart traffic lights, for example, if the lights use open and unencrypted protocols. The potential for attacks makes it imperative for cities, states and transit agencies to keep security top of mind when moving forward with IoT projects, says Robert Westervelt, a research manager for the Security Products group at market research firm IDC.
“It’s important to be concerned about it,” he adds, “and to make sure there is some thought behind the question of how an attacker can take advantage of new connections.”
SIGN UP: Get more news from the StateTech newsletter in your inbox every two weeks
Transport Agency Partnerships Can Keep Gadgets Safe

Fortunately, vendors are overwhelmingly taking steps to secure their products, says John Hibbard, director of operations for the Georgia Department of Transportation, which plans to deploy connected technology in state vehicles to give drivers information on when traffic lights will change. Already, the state employs a network of sensors and cameras from brands such as Axis to keep tabs on traffic.
“The challenge is, as a new gadget is introduced, ensuring that it plays well with the other gadgets, but also making sure that it doesn’t disturb the level of security that has been established,” Hibbard says. “It’s an ongoing effort.”
Delaware also plans to connect state vehicles and infrastructure and evaluate whether certain commercial systems are mature enough before allowing them to link to state sensors, says Gene Donaldson, operations manager of Delaware’s Transportation Management Center.
“It has to be a partnership among the agencies, the automobile manufacturers and the technology companies,” Donaldson says. “How do we tie all of this stuff together in a way that it’s secure, that it’s safe?”
Holistic Security Can Help Keep IoT Networks in the Clear
But even with security baked in to the design of devices, a good defense should incorporate the basic requirements of enterprise security. That includes inspecting devices for signs of damage or tampering during shipment, updating default passwords with a strong password, using two-factor authentication, and connecting devices to a private network that accepts only trusted systems, Westervelt says.
The installer should also check for any available device firmware updates and use only validated firmware from a manufacturer-approved location.
“Hopefully there is a mechanism for the device to check periodically for software updates,” Westervelt says, “but that is not always the case.”
Devices should only accept encrypted commands and requests from authenticated sources.
Some organizations that install multiple, critical devices will also segment them behind a firewall, making it more difficult for an attacker to use the connected devices to access more sensitive resources. If the devices collect and transmit data, the installer must also ensure that the transmission is encrypted and configured properly, Westervelt says. “Forensics investigators find a number of data breaches stemming from poorly implemented encryption each year,” he says.
Organizations also should have policies and procedures outlining device disposal.
“We’ve seen some data breaches stemming from this,” Westervelt says. “Mobile devices and PCs that should have had their hard drives removed and properly sanitized, had sensitive data on them, resulting in a reportable breach.”
Transport Agencies Should Learn From Past Mistakes
Tech observers point out that no IT system has ever been 100 percent secure, and that today’s non-IoT transportation environment already offers drivers and pedestrians plenty of risk.
“I don’t think we’ll ever get to zero risk,” says Doug Marsden, chief technical officer and vice president of research and development for the Ohio-based Transportation Research Center. That organization works with the state to create a $15 million Smart Mobility Corridor, outfitted with sensors and fiber-optic cable to provide more frequent and accurate traffic counts, as well as improve incident management and weather and surface-condition monitoring.
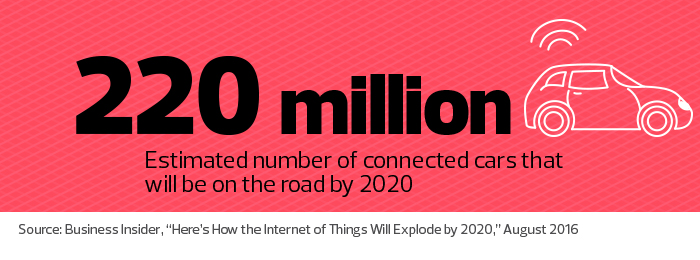 Still, Marsden says, agencies must make it difficult enough so that it isn’t worth hackers’ time to attempt attacks.
Still, Marsden says, agencies must make it difficult enough so that it isn’t worth hackers’ time to attempt attacks.
“It’s about various levels of security, so that nefarious hackers would have to break through several different layers of security before they could try to do anything like take control of a vehicle,” he says.
Despite the acknowledged risks, as Georgia gets ready to test IoT infrastructure on its highways, Hibbard focuses on the positive impacts that new connections might bring.
“You won’t have anybody running red lights,” he says. “And if you take it to the logical extreme, you won’t have cars hitting each other. It starts to have some interesting societal impacts. You think about insurance rates, you think about emergency rooms at hospitals.”
Agencies deploying IoT initiatives can take lessons from previous cyberattacks, Westervelt says. For example, some high-profile hacks are linked with organizations neglecting to continuously monitor the segmentation of their networks.
“Strike a balance between doom and gloom and say, ‘We’ve been down this road before, and this is what we’ve learned from the past,’” he says.









