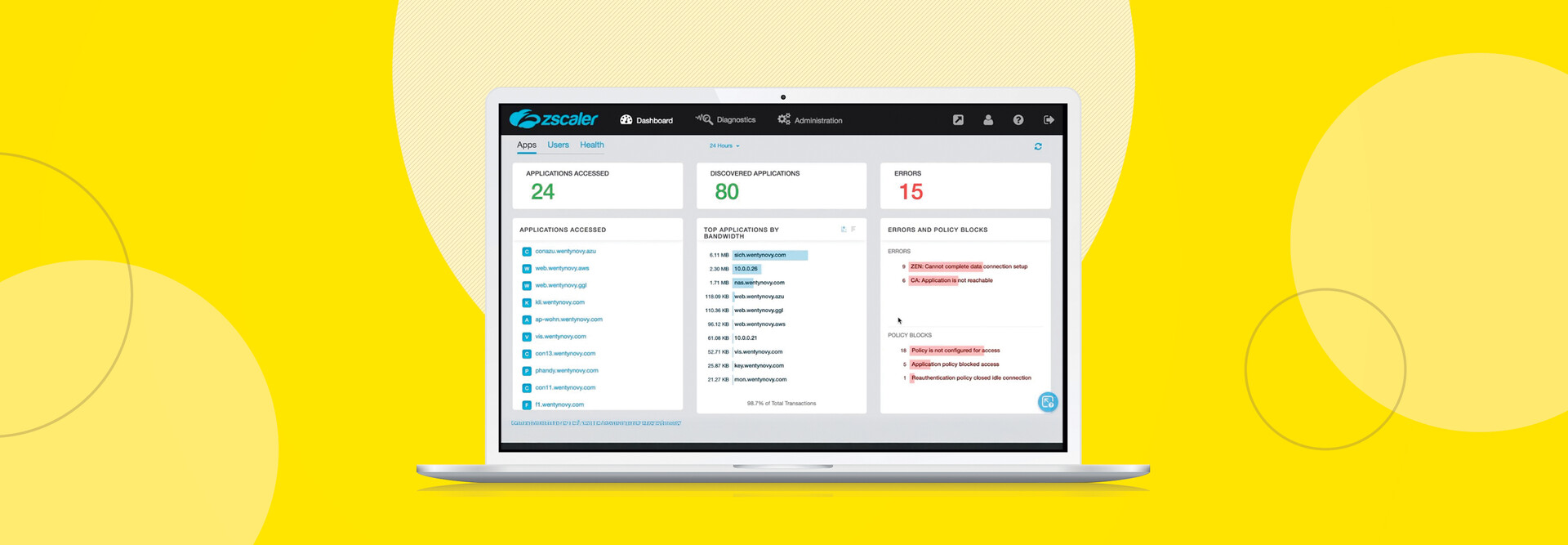
As a cloud-delivered, zero-trust network access solution, ZPA offers a compelling alternative to any state and local government agency looking to remove legacy VPNs or perimeter-based security models and move to something more scalable, sustainable and secure. Departments of all sizes could help IT security staff dramatically reduce cyber-risk while significantly improving application performance and productivity.
ZPA reduces the attack surface by hiding applications from the internet. I tested Zscaler by using the same application while traveling the farthest possible distance in the United States from my home network on the East Coast all the way to Hawaii. I wanted to see if we could detect any lag when using Zscaler in my home office compared with working from the Hawaiian Islands, far from all of my data and applications.
Reducing Exposure to Denial-of-Service Attacks
In Hawaii, I noticed that because all connections are outbound-only with ZPA, the solution effectively reduced exposure to specific types of attacks such as those that use denial-of-service techniques. The platform also removes all open, inbound firewall ports, further securing the network since the incoming traffic isn’t routed through an internal network. Instead, it’s brokered through the Zscaler cloud via lightweight Zscaler App Connectors.
While on the island of Oahu, I also noticed that the same rapid setup and integration to mission-critical applications occurred whether we were on the more remote north or western shores, at the center of the island or in the busy metropolitan center of Honolulu.
READ MORE: State governments automate user privileges to assist with identity management and access.
Accessing Internal Resources Without a Network
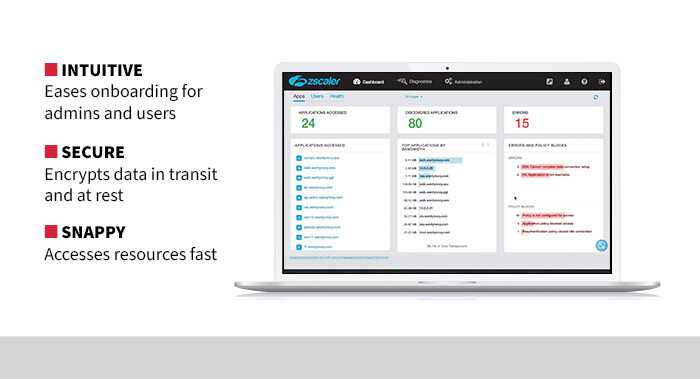
Unlike a traditional VPN, using Zscaler Private Access does not require users to connect to a network or establish direct paths to internal resources. As a software-defined, cloud-based solution, ZPA provides secure access to internal applications without placing users on the network. It uses a brokered, identity- and context-based authentication model to provide access to critical resources, based on zero-trust principles to ensure data security and integrity.
From a security operations center perspective, because ZPA separates application access from network access, the solution can reduce all attack vectors and the overall vulnerability surface, minimizing lateral movement. For CISOs, this capability empowers networks with a key security advantage for handling sensitive data. This approach also supports access to applications across multicloud environments, data centers and hybrid architectures, which makes it ideal for complex IT environments.