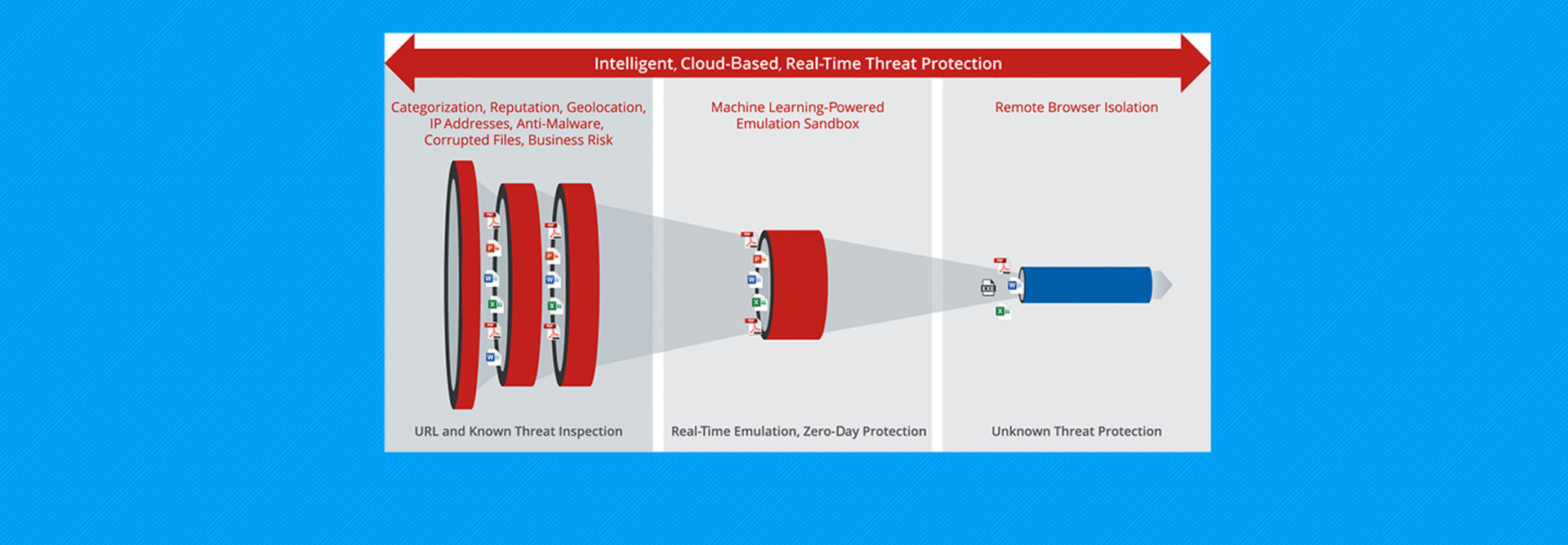
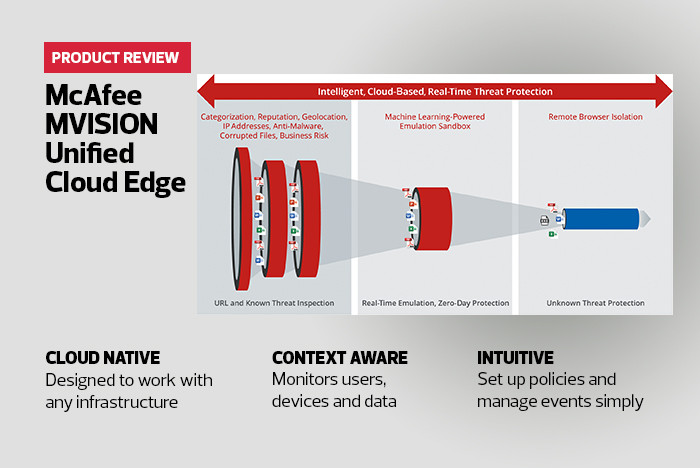
Tailoring Access with McAfee MVISION UCE
To test how the McAfee MVISION UCE platform handled various situations, I set up several precise rules for applications, users and processes. In all cases, the UCE handled traffic exactly how I specified. Whenever it did something incorrect, it was because I didn’t set the rules up just right. Working with the UCE is fairly straightforward, but since managers are basically configuring a zero-trust environment, it may take a little while to learn all the nuances of what this powerful program can achieve. McAfee can offer training to go with new deployments.
In the first scenario, I had a valid user with all correct passwords attempt to access a simulated state government network on a personal device. Per our policy, the user was given full access to the network but was prevented from downloading or uploading any files since a personal device not controlled by the state government was being used.
A second user was also valid and working on a state-owned asset. However, the security patches were not up to date, so the device was noncompliant with my security policy. In this case, the UCE gave the user the choice of interacting with the site using browser isolation (so it could not actually affect the network) or applying all of the patches and then, after the UCE verified that they were again compliant, accessing everything normally. It’s worth noting that assets owned by the organization need to have a UCE agent running on them to verify policies and provide better monitoring.
Yet another valid user with a state-owned device had active malware on the system. The user was denied access to the network and had future access revoked until a human administrator could verify that it was safe for the user to return.
In addition to managing users, McAfee UCE can also enforce rules regarding how cloud-based applications communicate with one another, or what happens when a previously unknown application tries to access network resources.
The UCE can even control tenant access. In one scenario, I was able to allow users to upload and download files freely to a state-operated Dropbox site, but added restrictions when dealing with personal Dropbox accounts. That can help to eliminate a serious security hole that can crop up with less advanced protection platforms.
Managing everything about cloud deployments, data and access from a single program is easily possible through the UCE. In every scenario tested, the UCE performed exactly as requested. This eliminated many vulnerabilities in the cloud-based test bed, ensured they stayed away and enabled total control of an entire cloud infrastructure from a single, user-friendly console.
McAfee MVISION Unified Cloud Edge
Technology: Cloud-based security software
Cloud Platforms: Amazon Web Services, Google Cloud, Microsoft Azure and many others
License Type: Annually per user
Maximum Users: Unlimited
Technical Support: Available 24/7