Vulnerabilities are highly sought after by attackers who use them to launch all kinds of nefarious activities, such as stealing data, implanting ransomware, escalating administrative privileges or launching advanced attacks.
A modern enterprise network can hold thousands or even millions of vulnerabilities, more than a large IT team could likely ever fix. And for many state governments with federated IT operations, this can be an even bigger issue as the hodgepodge of semi-independent agencies and organizations each contribute their own unique stack of vulnerabilities to that mix.
RELATED: How purple team exercises enhance threat management
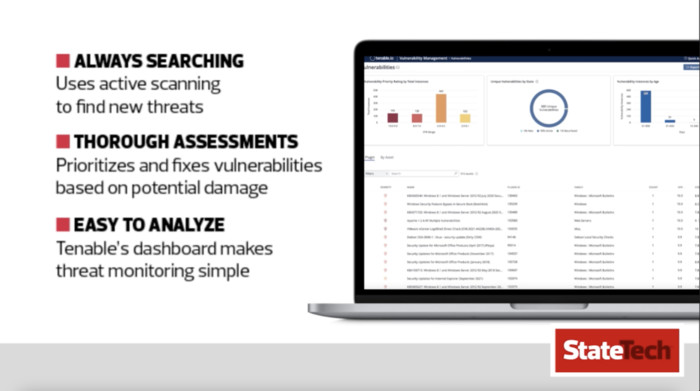
The Tenable Vulnerability Management platform (formerly Tenable.io) is deployed as a service and was designed to manage environments that are saturated with potential risks. It not only finds vulnerabilities but also is smart enough to prioritize which ones need to be fixed right away and which can wait until IT teams have time to address them.
Click the banner below for more on a proactive approach to maintaining a strong security posture.