Botnet Attacks: How City Governments Can Defend Against DDoS Attacks Fueled by IoT Botnets
As smart cities deploy more Internet of Things devices, they face a growing risk from botnet attacks, according to IT security experts.
“More devices mean more opportunities for botnets,” says Chris Wysopal, CTO and co-founder of application security firm Veracode. “Every connected device that has any kind of programmability is potentially going to become part of a botnet.”
Botnet attacks can take control of IoT devices in smart cities, making such IoT devices weaponized so that they can be used to launch distributed denial of service attacks. These DDoS attacks can send massive amounts of bandwidth to internet gateways and network devices to cripple connectivity to city websites, Wysopal notes. However, they can also be used in DDoS attacks at the application layer, sending traffic directly to IoT devices to tie up their computing power or starving them of resources that are not necessarily network related.
Mike Chapple, an associate teaching professor of IT, analytics and operations at the University of Notre Dame (and a StateTech contributor), says that as cities increase their dependence upon IoT technology, “it is important that they realize this dependence comes with increased technology risk,” and “one of those risks is the ability of a malicious attacker to conduct a DDoS attack, depriving a city of the use of their IoT devices.”
The threat comes as smart cities are booming. IDC expected smart city initiatives to attract technology investments of more than $81 billion globally in 2018, and spending is set to grow to $158 billion in 2022. Just the IoT technology revenues across 12 key smart city technologies and verticals will grow from around $25 billion in 2017 to $62 billion in 2026, according to ABI Research.
And as cities deploy more sensors and IP-connected devices for everything from traffic cameras to sensors that monitor infrastructure, they also run the risk of inviting more cyberattacks. Botnet attacks resulting from IoT vulnerabilities pose a serious risk that city governments need to guard against, experts say.
What Is a DDoS Attack?
A DDoS attack is a cyberattack in which multiple compromised systems attack a given target, such as a server or website, to deny users access to that target. Attackers often use compromised devices — desktops, laptops, smartphones or IoT devices — to command them to generate traffic to a website in order to disable it, in ways that the user does not even detect.
“The smart cybercriminal imposes limits on the malware code to avoid detection by not utilizing too much of the user’s bandwidth or system resources,” Carl Danowski, a CDW service delivery architect in managed services, writes in a blog post. “The user would have to know where to look to detect this, and probably won’t be motivated to as long as the software doesn’t cause any problems for them. The attack does not use just a single system but millions of such compromised systems, nearly simultaneously.”
The malware then visits or sends special network packets (OSI Layer 7 and Layer 3, respectively) to the website or DNS provider. The attack then generates what looks like, to most cybersecurity tools, normal traffic or unsuccessful connection attempts.
“However, the website soon becomes unavailable as some part of the infrastructure can no longer handle the sheer number of simultaneous requests,” Danowski notes. “It could be the router, the firewall, the web servers, the database servers behind the web servers — any number of points can become overwhelmed, leading to the unavailability of the service they are providing. As a result, legitimate users of the website are denied service.”
What Is a Botnet Attack?
Botnet, shorthand for “robot network,” attacks are related to DDoS attacks. Not all botnets are malicious; a botnet is a simply a group of connected computers working together to execute repetitive tasks, and can keep websites up and running. However, malicious botnets use malware to take control of internet-connected devices — such as smart city devices and IP-connected cameras — and then use them as a group to attack.
Importantly, these devices “are under the control of a single attacking party, known as the ‘bot-herder,’” Palo Alto Networks notes in a blog post. “Each individual machine under the control of the bot-herder is known as a bot. From one central point, the attacking party can command every computer on its botnet to simultaneously carry out a coordinated criminal action.”
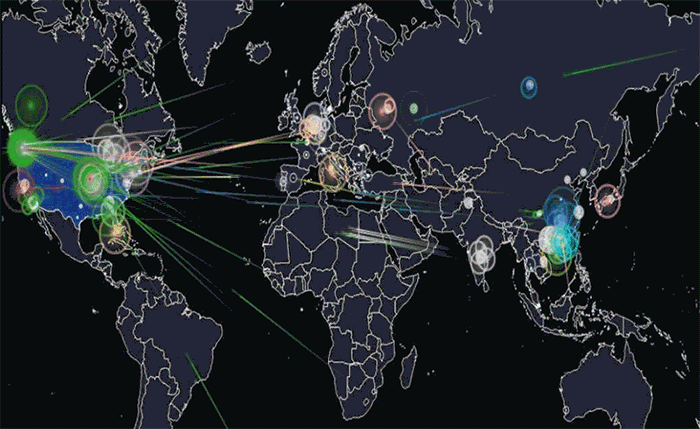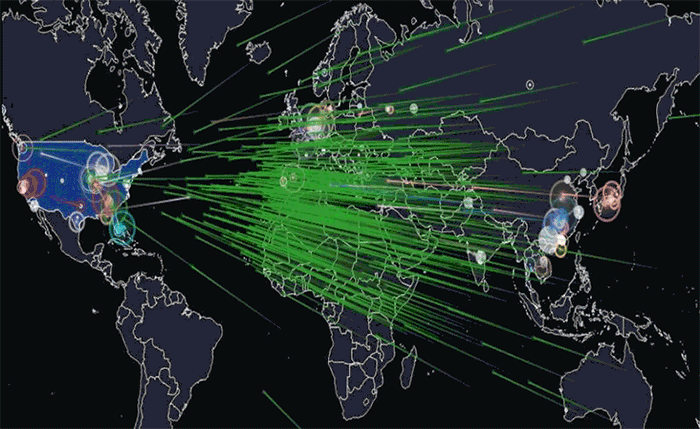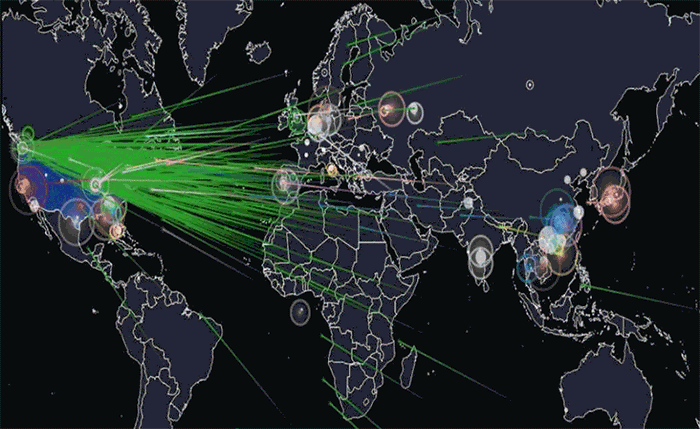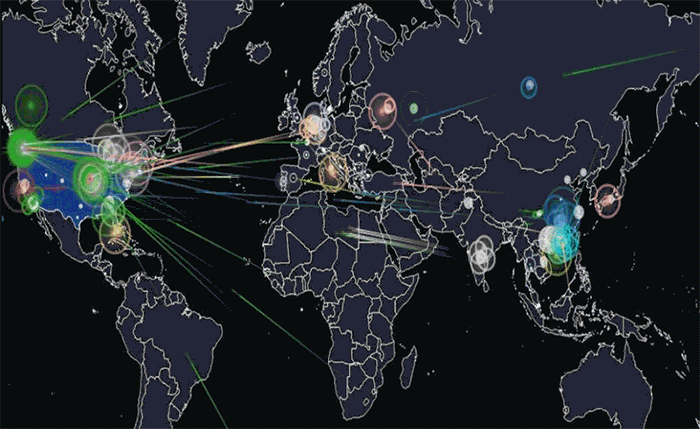
An illustration of the global Mirai botnet attack on DNS provider Dyn in October 2016. Photo: Joey Devilla/Wikimedia Commons
Botnets can sometimes be composed of millions of bots, which then enables the attacker to “perform large-scale actions that were previously impossible with malware,” Palo Alto adds.
What makes botnets especially nefarious in the world of cybersecurity is that, since they remain under control of a remote attacker, “infected machines can receive updates and change their behavior on the fly. As a result, bot-herders are often able to rent access to segments of their botnet on the black market for significant financial gain,” Palo Alto says in the blog post.
The Threats Botnet Attacks Pose for Smart Cities
Botnet attacks can take advantage of IoT vulnerabilities and lead to significant disruptions in services — not just of the affected IoT devices, but other systems and devices as well, experts say. Wysopal notes that although many IoT devices are placed behind firewalls or routers with network address translation, it is not impossible for attackers to gain access to them.
The National Institute of Standards and Technology is working on a draft document, “Considerations for Managing IoT Cybersecurity and Privacy Risks,” which notes that many IoT devices interact with the physical world in ways conventional IT devices usually do not. That means there are IoT vulnerabilities city IT admins need to be guarding against.
Further, NIST notes, many IoT devices “cannot be accessed, managed, or monitored in the same ways conventional IT devices can,” and the “availability, efficiency, and effectiveness of cybersecurity and privacy capabilities are often different for IoT devices than conventional IT devices.”
“If IoT devices are deployed and secured just like conventional IT devices, they will be much more likely to be not only exposed to DDoS and botnet attacks, but also vulnerable to compromise in order to force them to perform such attacks,” says Karen Scarfone, the principal consultant for Scarfone Cybersecurity (and a StateTech contributor).
If a city has deployed thousands of smart energy meters that all have a similar cybersecurity vulnerability, they could all be taken over in one botnet attack, Wysopal notes. Any time a city government is deploying a large number of similar IoT devices, which all may have the same vulnerability, “that botnet risk should be a part of your calculation” of how much time, resources and security will be needed to secure those devices.
Another aspect of the threat is that the botnet could be used to attack the city’s own networks and services, Wysopal says. “Leveraging maybe the smart meter devices to then go and attack the traffic network,” he says.
MORE FROM STATETECH: Discover how Massachusetts assessed its IoT vulnerabilities.
How Can City Governments Defend Against IoT Botnet Attacks?
As cities deploy IoT devices for smart cities projects, “they must include security planning into those discussions,” Chapple notes, if they want to ward off botnet attacks.
The “most important control” that cities can deploy is the use of network segmentation tools that isolate IoT devices from the internet at large, Chapple says. That will limit the spread of an attack that exploits IoT vulnerabilities. “Placing IoT devices on a segmented network prevents external traffic from reaching them and reduces their vulnerability to DDoS and other attacks,” he says.
“One of the important things is to design these networks such that your average government worker’s computer, which may be connected to the office Wi-Fi, can’t talk to the IoT devices that are running a smart city, with segmentation” Wysopal adds. “The risk is attacking an employee’s computer and then using that as a stepping stone to get to these Internet of Things networks.”
To guard against DDoS and botnet attacks, city IT departments should also deploy network monitoring and intrusion detection solutions that can detect when botnets are using are attempting to connect with known command and control servers, Wysopal says. Intrusion detection systems can detect if compromised workstations are scanning the network for vulnerabilities, for example. However, that detection will likely come after a device or series of devices have already been compromised.
As they work to counter the botnet threat, city network managers can deploy network performance monitoring and diagnostic tools, which can give them a baseline for network traffic so they can determine if something is anomalous.
A key element of guarding against botnet attacks and IoT vulnerabilities is for cities to not deploy devices that have vulnerabilities to begin with, Wysopal says. Before a city purchases and deploys IoT devices, it needs to work with vendors to ensure basic cybersecurity practices are followed, such as not having hard-coded passwords. Additionally, if a vulnerability is discovered and becomes widely known, cities should know how quickly their IoT devices can be patched and updated and how much work that will require.
“Once a vulnerability becomes public, there’s that risk. Attackers will start to go after all devices of that type,” he says. “if your city has deployed those devices, you’re at risk until you update. So how easy has the vendor made the update process?” City IT leaders should also determine that vendors are using secure coding practices to create software for their IoT devices.
Aside from network segmentation, intrusion detection and supply chain security, there are also basic cybersecurity measures cities can take to protect IoT devices. The NIST publication provides a draft list of 15 cybersecurity and privacy capabilities all organizations should consider implementing for their IoT devices, Scarfone notes.
“The first one is the ability to identify each IoT device both logically and physically. An agency may take it for granted that they can identify every device, but in the IoT world this is not the case,” she says. “If a DDoS attack occurs, the agency may need to be able to rapidly identify affected devices or, if the agency’s own devices are performing the DDoS attack, which devices are responsible.”
Other steps include having an inventory of the software on each IoT device, having the ability to securely patch each IoT device and control configuration changes, and having the ability to control local and remote access to each IoT device, Scarfone notes.
“These are all generally taken for granted in the conventional IT world, but many IoT devices do not offer all these capabilities,” she says. “To compensate for this, agencies may need to use network-based security controls, such as firewalls and gateways, instead of relying on controls within individual IoT devices.”





.jpg)



